For Telegram users, there is also Telegram: Contact @tor_bridges
We need testers to check if our new default bridge is blocked in your ISP. Thanks!
Yota, Beeline, Tele2 — all blocked, as well as my test relay, which was reachable 15 hours ago.
ISP “tiera” from Saint-Petersburg with TSPU. Tor is blocked
When you say “all blocked,” are you talking about the new default bridge mentioned by @gus?
Yes. This new relay is not accessible from these ISP.
So if I am reading this thread correctly, the situation today is:
Blocked
- Tor project website
- Unobfuscated relays
- Widely publicized obfs4 bridges
Open for now
- Tor project website mirrors
- Snowflake alpha with newest patch
- Newly added obfs4 bridges
- Meek-azure ?
Last resorts
- Private obfs4 bridges
- Private pre-proxy (V2Ray or Shadowsocks)
The “last resorts” are limited to those who have the resources to set up a private server, which they could possibly share with trusted contacts.
Not all of them. I requested some public bridges and they worked
Also, i use tunelled ipv6 and its not filtered
This in torrc worked :
ClientUseIPv4 0
ClientUseIPv6 1
I don’t know whether TSPU equipped ISPs with ipv6 also block ipv6 tor entry ips
Only a few ISPs in Russia have ipv6
ER-Telecom — IPv6 bridges are working fine and all IPv4 bridges are blocked. YOTA — all blocked.
There are three main bridge distribution methods:
-
https(the Tor Project website) -
moat(inside Tor Browser) -
email(send request from Gmail or Riseup email address)
If the Tor Project website is blocked, then so is https. That leaves only moat or email.
It would be interesting to know which method censors are using to discover bridge IP addresses to block. Then volunteers setting up new bridges could use the opposite method.
I thought that BridgeDB did not give out IPv6 bridges. Has that changed? Last time I checked, it was not possible to obtain an IPv6 obfs4 bridge from BridgeDB. It was only possibly to obtain “vanilla” (i.e. unencrypted) IPv6 bridges.
Method of testing: Go to https://bridges.torproject.org/options and check the box for " Do you need IPv6 addresses?" If you also request obfs4, you get an error message, BridgeDB encountered an error. There currently aren't any bridges available... Perhaps you should try going back and choosing a different bridge type!
You mean all the built-in IPv4 bridges? Surely not all 1,500 total IPv4 bridges in BridgeDB are blocked?
Yes, you are right, currently birdgedb doesn’t distribute IPv6 bridges. We want to fix that, but it will take some time:
But Tor Browser comes with a IPv6 bult-in bridge, maybe @quantalFox means that bridge? Or you could set up your own bridge and use it’s IPv6.
Alright, here’s a new vanilla Tor bridge (IPv4 or IPv6):
5.161.66.77:55882
[2a01:4ff:f0:214d::1]:55882
obfs4 bridge:
Bridge obfs4 5.161.66.77:55441 F3EABDE3937418457B993A03F0B2BFDED55B2CB4 cert=xHA5BH3ch7U3nH7W1NEw9L0lAHs2zc3Uc0z/Od74g8eJ5+O/TEgK7dZKdmJ9FqBDZgptOQ iat-mode=0
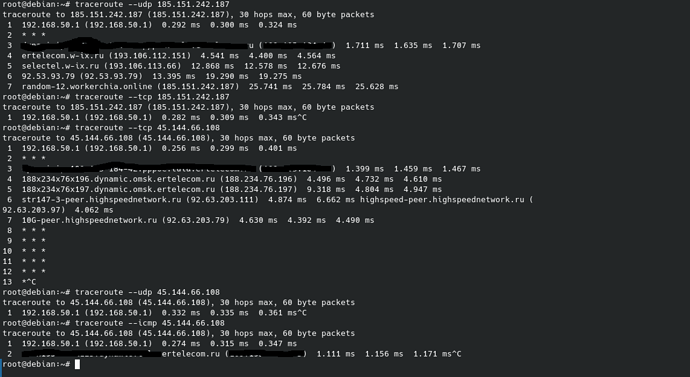
Первый IP (185.151.242.187) - нода, созданная до блокировки Tor, летят в таймаут все подключения по TCP.
Второй IP (45.144.66.108) - нода, созданная после блокировки Tor, дропаются все подключения.
Оба IP на скрине доступны с VPN, провайдер - ДОМРУ
Right now about 12.9% of Tor nodes are reachable from ISP with TSPU DPI systems.
Nmap done: 6702 IP addresses (868 hosts up)
How I tested that:
- Extracted router IP addresses from
/var/lib/tor/cached-descriptorsfile of long-running Tor relay - Executed nmap scan from Russian filtered network:
nmap -iL input.txt -n -PS22,80,443,9001 -sn -T4(remember, TSPU blocks only TCP connectivity, that’s why we can’t rely on default nmap’s ICMP reachability test — this would be false positive). - Used some of found
ip:port fingerprintcombination as a bridge, confirmed that the connection succeeded.
This could be used to enumerate working IP addresses and publish them as bridges.
Good work. So now the list of ways to reach the Tor network goes:
Open for now
- Snowflake bridge in Tor Browser 11.5a1 release candidate
- Not-yet-blocked obfs4 bridges, hundreds added recently
- Not-yet-blocked relays used as vanilla bridges
- Meek-azure – has anyone tested this?
Last resorts
- Private obfs4 bridges
- Private pre-proxy (SS/v2ray)
meek-azure works fine. They’ve unblocked ajax.aspnetcdn.com.
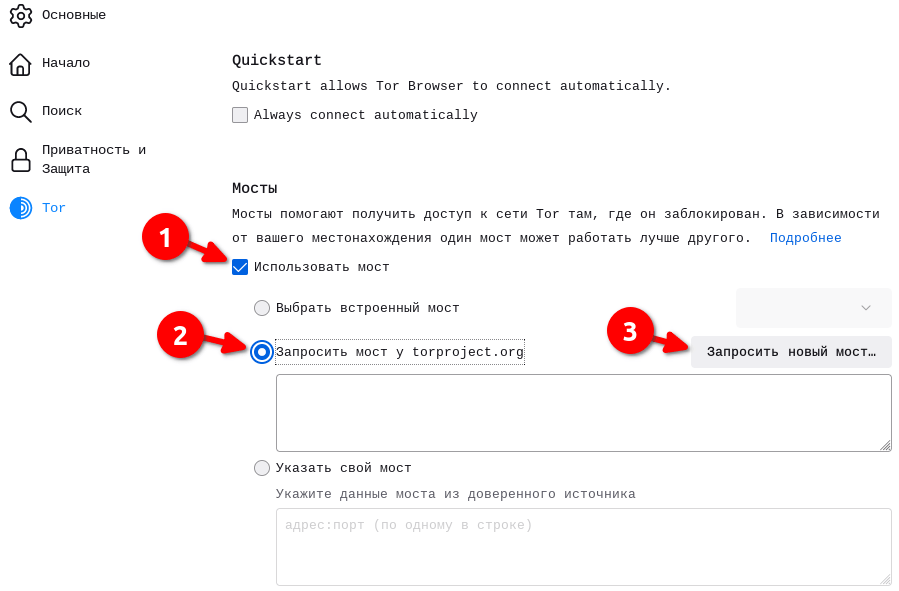
Пользователи из России могут запросить мосты через механизм «запросить мост у torproject.org», встроенный в Tor Browser. По состоянию на 16 декабря мосты, получаемые через этот механизм, работают у всех провайдеров РФ.
В десктопном браузере это делается так (страница настроек):
Более подробная информация о других способах обхода блокировок Tor: Tor blocked in Russia: how to circumvent censorship - Censorship Circumvention - Tor Project Forum