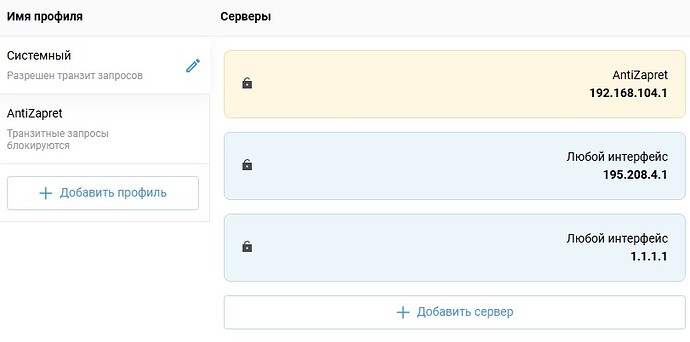
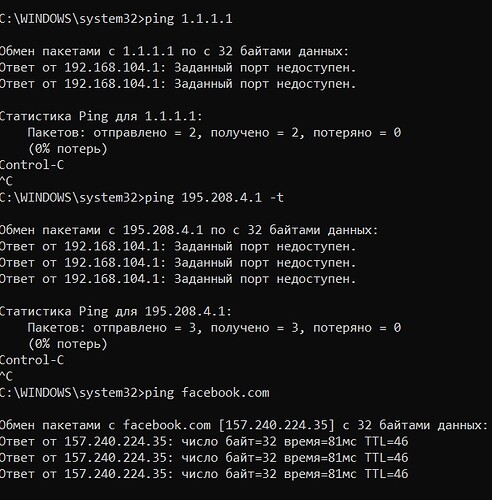
Я ранее писал, что у меня проблемы с antizapret и грешил на днс и кажется отловил ошибку, антизапрет перестаёт работать как и весь интернет, если у меня есть doh и dot днс для ИИ (как указано в инструкции). Есть ли какое то решение для этой проблемы? Уж очень хочется пользоваться chetgpt итд.
Ps. Антизапрет с dot и doh работает примерно от 1 дня до 3. В чем потом причина отвала не понимаю.
Простите если не по теме. Животрепещущий вопрос. Поставил наконец AdGuard Home на Entware. Ultra 1811. Перестал работать KeenDNS в принципе. Объясните пожалуйста куда мне что нужно прописать, чтобы починить? Всё делал согласно инструкции + свой ресёрч, но про конкретно KeenDNS не совсем понял.
pull-filter ignore тут вообще никаким боком.
Эта команда приказывает игнорировать директиву “блокировать внешние DNS”, пришедшую от сервера, потому что в Linux блокировка внешних DNS в OVPN не поддерживается.
Слабо верится, что проблема в них. Больше смахивает на проблему на сервере АнтиЗапрета.
Решение: арендовать свой сервер, поднять там свой АнтиЗапрет и добавлять туда домены ИИ-сервисов.
У меня не родной Keenetic, поэтому KeenDNS не работает и его работу я не могу проверить.
Попробуйте спросить на официальном форуме или в тех. поддержке.
На старой прошивке перестал подключаться к антизапрету. Обновил до 4.2.3. всё тоже самое. днс был 8.8.8.8 поменял на 1.1.1.1 не помогло. Есть какое то решение для стабильной работы?
Добавляйте строчку verb 5 в конфиг и смотрите системный журнал.
Возможно, ваш провайдер начал блокировать протокол OpenVPN.
Что-то последнее время, несколько дней как, стало особенно туговато, чуть ли не каждый день отваливается, и нащупать потом переподключением рабочий серв АЗ далеко не с первого раза получается. Самое гадкое, вот так вечером после очередного падения вроде подключаешься кое-как, проверяешь, что всё ок, а на утро только проснёшься - домашние уже бухтят, что нифига не открывается ![]()
Лучше арендовать сервер и развернуть там свою копию АнтиЗапрета. Заодно и произвольные домены типа YT можно проксировать.
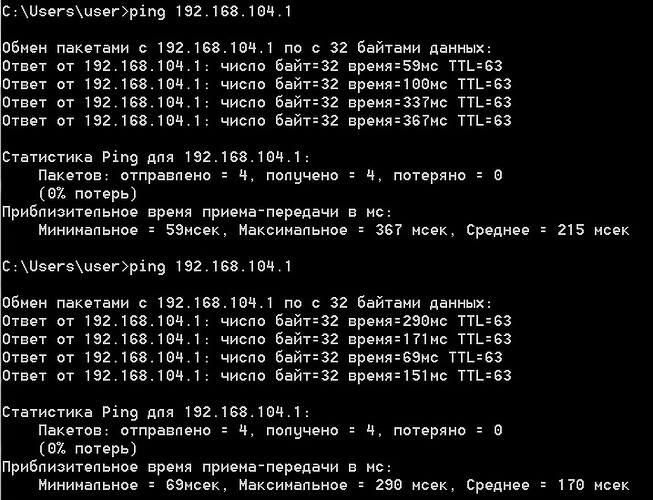
Ради интереса: когда оно опять засбоит, пинганите 192.168.104.1
Будет он отвечать на пинги или нет?
В разделе про доступ к ИИ-сервисам обновлены адреса Comss DNS. Старые адреса перестанут работать в ближайшие дни.
Да уж, насчёт альтернативных вариантов вроде своего сервера уже появлялись мысли
Сейчас вечером снова отвалилось, попробовал:
Спасибо. Была мысль просто пинговать сервер в цикле и передёргивать подключение, если сервер недоступен. Но раз он пингуется, то придётся придумывать более сложное решение.
Что то отвалы пошли каждый день, непонятно что случилось с АЗ или в прошивке кинетика дело(((
Ни смена днс , ни отказ от doh/dot , ничего не помогает
Раз проблема на сервере, то, разумеется, жонглирование настройками на клиенте не поможет. Поможет передергивание подключения до тех пор, пока вас не перекинет на сервер, который не испытывает проблем.
Добрый день. Вчера началась проблема с работой сайтов вне личного впн Антизапрет. То, что открывает Антизапрет работает, остальные сайты не открываются(зона РУ). Роутеры кинетик, несколько штук на разных провайдерах. Настроено по этой инструкции, файл свой с сервера., версия сервера 3 месяца назад ставил еще.
Помогите побороть, не очень шарю.
Маршруты при выкл
Спойлер
| 0.0.0.0/0 | 192.168.88.1 | Ethernet-подключение |
|---|---|---|
| 89.110.103.106/32 | 192.168.88.1 | Ethernet-подключение |
| 192.168.1.0/24 | 0.0.0.0 | Домашняя сеть |
| 192.168.88.0/24 | 0.0.0.0 | Ethernet-подключение |
Маршруты при включенном
Спойлер
| Адрес назначения | Шлюз | Интерфейс |
|---|---|---|
| 0.0.0.0/0 | 192.168.88.1 | Ethernet-подключение |
| 1.1.1.1/32 | 192.168.104.1 | AntiZapret |
| 10.224.0.0/15 | 192.168.104.1 | AntiZapret |
| 68.171.224.0/19 | 192.168.104.1 | AntiZapret |
| 74.82.64.0/19 | 192.168.104.1 | AntiZapret |
| 89.110.103.106/32 | 192.168.88.1 | Ethernet-подключение |
| 103.246.200.0/22 | 192.168.104.1 | AntiZapret |
| 178.239.88.0/21 | 192.168.104.1 | AntiZapret |
| 185.104.45.0/24 | 192.168.104.1 | AntiZapret |
| 192.168.1.0/24 | 0.0.0.0 | Домашняя сеть |
| 192.168.88.0/24 | 0.0.0.0 | Ethernet-подключение |
| 192.168.104.0/22 | 0.0.0.0 | AntiZapret |
| 192.168.104.1/32 | 0.0.0.0 | AntiZapret |
| 193.105.213.36/30 | 192.168.104.1 | AntiZapret |
| 195.208.4.1/32 | 192.168.104.1 | AntiZapret |
| 203.104.128.0/20 | 192.168.104.1 | AntiZapret |
| 203.104.144.0/21 | 192.168.104.1 | AntiZapret |
| 203.104.152.0/22 | 192.168.104.1 | AntiZapret |
Было такое, помогло убиение контейнера, удаление всех образов докера и создание контейнера заново (у меня АЗ крутится в докере).
Больше смахивает на проблему с сервером.
Добрый день. Помогите с настройкой пожалуйста) Сменил провайдера и перестало работать. Удалил старое подключение,создал новое , но никак не подключается
Добавьте в конфиг строчку verb 5 и покажите системный журнал.
Возможно, новый провайдер просто блокирует протокол.
Спойлер
Dec 14 10:58:10 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:58:10 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:58:10 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:58:10 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:09 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:09 ndm
Error: Service: “OpenVPN0”: unexpectedly stopped.
Dec 14 10:58:09 OpenVPN0
Error: Exiting due to fatal error
Dec 14 10:58:09 OpenVPN0
Error: Cannot load inline certificate file
Dec 14 10:58:09 OpenVPN0
Warning: OpenSSL: error:0A080009:lib(20)::reason(524297):
Dec 14 10:58:09 OpenVPN0
Warning: OpenSSL: error:04800066:lib(9)::reason(102):
Dec 14 10:58:09 OpenVPN0
Info: DCO version: N/A
Dec 14 10:58:09 OpenVPN0
Info: library versions: OpenSSL 3.0.15 3 Sep 2024, LZO 2.10
Dec 14 10:58:09 OpenVPN0
Info: OpenVPN 2.6.7 [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
Dec 14 10:58:07 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:58:07 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:58:07 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:58:07 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:06 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:06 ndm
Error: Service: “OpenVPN0”: unexpectedly stopped.
Dec 14 10:58:06 OpenVPN0
Error: Exiting due to fatal error
Dec 14 10:58:06 OpenVPN0
Error: Cannot load inline certificate file
Dec 14 10:58:06 OpenVPN0
Warning: OpenSSL: error:0A080009:lib(20)::reason(524297):
Dec 14 10:58:06 OpenVPN0
Warning: OpenSSL: error:04800066:lib(9)::reason(102):
Dec 14 10:58:06 OpenVPN0
Info: DCO version: N/A
Dec 14 10:58:06 OpenVPN0
Info: library versions: OpenSSL 3.0.15 3 Sep 2024, LZO 2.10
Dec 14 10:58:06 OpenVPN0
Info: OpenVPN 2.6.7 [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
Dec 14 10:58:04 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:58:04 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:58:04 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:58:04 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:03 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:03 ndm
Error: Service: “OpenVPN0”: unexpectedly stopped.
Dec 14 10:58:03 OpenVPN0
Error: Exiting due to fatal error
Dec 14 10:58:03 OpenVPN0
Error: Cannot load inline certificate file
Dec 14 10:58:03 OpenVPN0
Warning: OpenSSL: error:0A080009:lib(20)::reason(524297):
Dec 14 10:58:03 OpenVPN0
Warning: OpenSSL: error:04800066:lib(9)::reason(102):
Dec 14 10:58:03 OpenVPN0
Info: DCO version: N/A
Dec 14 10:58:03 OpenVPN0
Info: library versions: OpenSSL 3.0.15 3 Sep 2024, LZO 2.10
Dec 14 10:58:03 OpenVPN0
Info: OpenVPN 2.6.7 [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
Dec 14 10:58:01 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:58:01 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:58:01 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:58:01 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:00 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:58:00 ndm
Error: Service: “OpenVPN0”: unexpectedly stopped.
Dec 14 10:58:00 OpenVPN0
Error: Exiting due to fatal error
Dec 14 10:58:00 OpenVPN0
Error: Cannot load inline certificate file
Dec 14 10:58:00 OpenVPN0
Warning: OpenSSL: error:0A080009:lib(20)::reason(524297):
Dec 14 10:58:00 OpenVPN0
Warning: OpenSSL: error:04800066:lib(9)::reason(102):
Dec 14 10:58:00 OpenVPN0
Info: DCO version: N/A
Dec 14 10:58:00 OpenVPN0
Info: library versions: OpenSSL 3.0.15 3 Sep 2024, LZO 2.10
Dec 14 10:58:00 OpenVPN0
Info: OpenVPN 2.6.7 [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
Dec 14 10:57:58 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:57:58 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:57:58 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:57:58 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:57:57 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:57:57 ndm
Error: Service: “OpenVPN0”: unexpectedly stopped.
Dec 14 10:57:57 OpenVPN0
Error: Exiting due to fatal error
Dec 14 10:57:57 OpenVPN0
Error: Cannot load inline certificate file
Dec 14 10:57:57 OpenVPN0
Warning: OpenSSL: error:0A080009:lib(20)::reason(524297):
Dec 14 10:57:57 OpenVPN0
Warning: OpenSSL: error:04800066:lib(9)::reason(102):
Dec 14 10:57:57 OpenVPN0
Info: DCO version: N/A
Dec 14 10:57:57 OpenVPN0
Info: library versions: OpenSSL 3.0.15 3 Sep 2024, LZO 2.10
Dec 14 10:57:57 OpenVPN0
Info: OpenVPN 2.6.7 [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
Dec 14 10:57:55 ndm
Info: Core::System::StartupConfig: configuration saved.
Dec 14 10:57:55 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:57:55 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:57:55 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:57:55 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:57:54 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:57:54 ndm
Error: Service: “OpenVPN0”: unexpectedly stopped.
Dec 14 10:57:54 OpenVPN0
Error: Exiting due to fatal error
Dec 14 10:57:54 OpenVPN0
Error: Cannot load inline certificate file
Dec 14 10:57:54 OpenVPN0
Warning: OpenSSL: error:0A080009:lib(20)::reason(524297):
Dec 14 10:57:54 OpenVPN0
Warning: OpenSSL: error:04800066:lib(9)::reason(102):
Dec 14 10:57:54 OpenVPN0
Info: DCO version: N/A
Dec 14 10:57:54 OpenVPN0
Info: library versions: OpenSSL 3.0.15 3 Sep 2024, LZO 2.10
Dec 14 10:57:54 OpenVPN0
Info: OpenVPN 2.6.7 [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
Dec 14 10:57:52 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: local endpoint is “192.168.1.2”.
Dec 14 10:57:52 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: connecting via “ISP” (GigabitEthernet1).
Dec 14 10:57:52 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: remote endpoint is “1.2.3.4”.
Dec 14 10:57:52 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:57:51 ndm
Info: Core::System::StartupConfig: saving (coala/rci).
Dec 14 10:57:51 ndm
Info: Network::Interface::Base: “OpenVPN0”: interface is up.
Dec 14 10:57:51 ndm
Info: Network::Interface::Base: “OpenVPN0”: “base” changed “conf” layer state “disabled” to “running”.
Dec 14 10:57:39 ndm
Info: Core::System::StartupConfig: configuration saved.
Dec 14 10:57:36 ndm
Info: Network::Interface::EndpointTracker: “OpenVPN0”: added a host route to 1.2.3.4 via 192.168.1.1 (GigabitEthernet1).
Dec 14 10:57:35 ndm
Info: Core::System::StartupConfig: saving (coala/rci).
Dec 14 10:57:35 ndm
Info: Network::Interface::Base: “OpenVPN0”: schedule cleared.
Dec 14 10:57:35 ndm
Info: Network::Interface::Base: “OpenVPN0”: interface is down.
Dec 14 10:57:35 ndm
Info: OpenVpn::Interface: “OpenVPN0”: set connection via any interface.
Dec 14 10:57:35 ndm
Info: OpenVpn::Interface: “OpenVPN0”: enable automatic routes accept via tunnel.
Dec 14 10:57:35 ndm
Info: OpenVpn::Interface: “OpenVPN0”: configuration successfully saved.
Dec 14 10:57:35 ndm
Info: Network::Interface::Ip: “OpenVPN0”: TCP-MSS adjustment disabled.
Dec 14 10:57:35 ndm
Info: Dns::InterfaceSpecific: “OpenVPN0”: cleared IPv4 static name server list.
Dec 14 10:57:35 ndm
Info: Network::Interface::Ip: “OpenVPN0”: IP address cleared.
Dec 14 10:57:35 ndm
Info: Network::Interface::Base: “OpenVPN0”: assigned role “misc” for OpenVPN0.
Dec 14 10:57:35 ndm
Info: Network::Interface::Base: “OpenVPN0”: deleted all roles.
Dec 14 10:57:35 ndm
Info: Network::Interface::Base: “OpenVPN0”: description saved.
Dec 14 10:57:35 ndm
Info: Network::Interface::Supplicant: “OpenVPN0”: authentication is unchanged.
Dec 14 10:57:11 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) had deauthenticated by AP (reason: due to BSS transition management).
Dec 14 10:56:10 ndhcps
Info: sending ACK of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:56:09 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.142 from 7c:f6:66:84:cc:8d.
Dec 14 10:56:09 ndhcps
Info: making OFFER of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:56:09 ndhcps
Info: DHCPDISCOVER received from 7c:f6:66:84:cc:8d.
Dec 14 10:56:09 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) set key done in WPA2/WPA2PSK.
Dec 14 10:56:09 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had associated.
Dec 14 10:50:35 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had deauthenticated by AP (reason: GTK 2-way handshake timeout).
Dec 14 10:50:35 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) group key handshaking timeout.
Dec 14 10:49:40 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(3c:0b:4f:59:92:36) GTK rekey done, group cipher AES.
Dec 14 10:49:40 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) GTK rekey done, group cipher AES.
Dec 14 10:47:26 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(be:19:72:6b:8f:54) had deauthenticated by AP (reason: due to BSS transition management).
Dec 14 10:47:26 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) had re-associated from 50:ff:20:53:a4:dd (FT roam).
Dec 14 10:47:26 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) FT authenticated successfully.
Dec 14 10:42:51 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) had deauthenticated by AP (reason: due to BSS transition management).
Dec 14 10:42:51 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(be:19:72:6b:8f:54) had re-associated from 50:ff:20:53:a4:db (FT roam).
Dec 14 10:42:51 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(be:19:72:6b:8f:54) FT authenticated successfully.
Dec 14 10:42:32 bndstrg
Info: band steering: send BTM request to be:19:72:6b:8f:54 for roam to 2.4GHz band (Low RSSI: -85)
Dec 14 10:42:25 bndstrg
Info: band steering: send BTM request to be:19:72:6b:8f:54 for roam to 2.4GHz band (Low RSSI: -80)
Dec 14 10:42:20 bndstrg
Info: band steering: send BTM request to be:19:72:6b:8f:54 for roam to 2.4GHz band (Low RSSI: -82)
Dec 14 10:42:14 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(be:19:72:6b:8f:54) had deauthenticated by AP (reason: due to BSS transition management).
Dec 14 10:42:14 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) had re-associated from 50:ff:20:53:a4:dd (FT roam).
Dec 14 10:42:14 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) FT authenticated successfully.
Dec 14 10:41:29 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) had deauthenticated by AP (reason: due to BSS transition management).
Dec 14 10:41:29 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(be:19:72:6b:8f:54) had re-associated from 50:ff:20:53:a4:db (FT roam).
Dec 14 10:41:29 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(be:19:72:6b:8f:54) FT authenticated successfully.
Dec 14 10:41:20 bndstrg
Info: band steering: send BTM request to be:19:72:6b:8f:54 for roam to 2.4GHz band (Low RSSI: -86)
Dec 14 10:41:15 bndstrg
Info: band steering: send BTM request to be:19:72:6b:8f:54 for roam to 2.4GHz band (Low RSSI: -81)
Dec 14 10:41:12 ndhcps
Info: sending ACK of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:41:12 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.142 from 7c:f6:66:84:cc:8d.
Dec 14 10:41:12 ndhcps
Info: making OFFER of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:41:12 ndhcps
Info: DHCPDISCOVER received from 7c:f6:66:84:cc:8d.
Dec 14 10:41:12 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) set key done in WPA2/WPA2PSK.
Dec 14 10:41:12 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had associated.
Dec 14 10:41:10 bndstrg
Info: band steering: send BTM request to be:19:72:6b:8f:54 for roam to 2.4GHz band (Low RSSI: -81)
Dec 14 10:36:49 ndhcps
Info: sending ACK of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:36:48 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.142 from 7c:f6:66:84:cc:8d.
Dec 14 10:36:48 ndhcps
Info: making OFFER of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:36:48 ndhcps
Info: DHCPDISCOVER received from 7c:f6:66:84:cc:8d.
Dec 14 10:36:48 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) set key done in WPA2/WPA2PSK.
Dec 14 10:36:48 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had associated.
Dec 14 10:35:34 ndhcps
Info: sending ACK of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:35:34 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.142 from 7c:f6:66:84:cc:8d.
Dec 14 10:35:34 ndhcps
Info: making OFFER of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 10:35:34 ndhcps
Info: DHCPDISCOVER received from 7c:f6:66:84:cc:8d.
Dec 14 10:35:34 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) set key done in WPA2/WPA2PSK.
Dec 14 10:35:34 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had associated.
Dec 14 10:26:59 ndhcps
Info: sending ACK of 192.168.0.127 to 3c:0b:4f:59:92:36.
Dec 14 10:26:58 ndhcps
Info: DHCPREQUEST received (STATE_RENEWING) for 192.168.0.127 from 3c:0b:4f:59:92:36.
Dec 14 10:16:11 ndhcps
Info: sending ACK of 192.168.0.38 to 74:5e:1c:30:12:ad.
Dec 14 10:16:10 ndhcps
Info: DHCPREQUEST received (STATE_RENEWING) for 192.168.0.38 from 74:5e:1c:30:12:ad.
Dec 14 10:01:21 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had been aged-out and disassociated (idle silence).
Dec 14 09:50:47 ndhcps
Info: sending ACK of 192.168.0.135 to 50:ff:20:5c:83:16.
Dec 14 09:50:47 ndhcps
Info: sending ACK of 10.1.30.142 to 52:ff:20:5c:83:15.
Dec 14 09:50:47 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.135 from 50:ff:20:5c:83:16.
Dec 14 09:50:47 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 10.1.30.142 from 52:ff:20:5c:83:15.
Dec 14 09:50:47 ndhcps
Info: making OFFER of 192.168.0.135 to 50:ff:20:5c:83:16.
Dec 14 09:50:47 ndhcps
Info: DHCPDISCOVER received from 50:ff:20:5c:83:16.
Dec 14 09:50:47 ndhcps
Info: making OFFER of 10.1.30.142 to 52:ff:20:5c:83:15.
Dec 14 09:50:47 ndhcps
Info: DHCPDISCOVER received from 52:ff:20:5c:83:15.
Dec 14 09:50:45 kernel
Info: br1: topology change detected, propagating
Dec 14 09:50:45 kernel
Info: br1: port 1(eth2.2) received tcn bpdu
Dec 14 09:50:45 kernel
Info: br0: topology change detected, propagating
Dec 14 09:50:45 kernel
Info: br0: port 1(eth2.1) received tcn bpdu
Dec 14 09:50:37 ndhcps
Info: sending ACK of 10.1.30.142 to 52:ff:20:5c:83:15.
Dec 14 09:50:37 ndhcps
Info: sending ACK of 192.168.0.135 to 50:ff:20:5c:83:16.
Dec 14 09:50:37 ndhcps
Info: DHCPREQUEST received (STATE_RENEWING) for 192.168.0.135 from 50:ff:20:5c:83:16.
Dec 14 09:50:37 ndhcps
Info: DHCPREQUEST received (STATE_RENEWING) for 10.1.30.142 from 52:ff:20:5c:83:15.
Dec 14 09:50:36 ndhcps
Info: sending ACK of 192.168.0.148 to 00:e0:4c:68:02:7b.
Dec 14 09:50:35 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.148 from 00:e0:4c:68:02:7b.
Dec 14 09:50:35 ndhcps
Info: making OFFER of 192.168.0.148 to 00:e0:4c:68:02:7b.
Dec 14 09:50:35 ndhcps
Info: DHCPDISCOVER received from 00:e0:4c:68:02:7b.
Dec 14 09:50:29 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(02:be:13:52:a5:e7) FT authentication rejected (status code: 53).
Dec 14 09:48:13 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) GTK rekey done, group cipher AES.
Dec 14 09:48:13 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(be:19:72:6b:8f:54) replay counter differs in key handshaking (msg 2 of 2-way).
Dec 14 09:48:12 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(3c:0b:4f:59:92:36) GTK rekey done, group cipher AES.
Dec 14 09:47:59 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) GTK rekey done, group cipher AES.
Dec 14 09:34:06 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster1/AccessPoint0”: STA(1a:fa:8b:a3:de:90) had deauthenticated by AP (reason: due to BSS transition management).
Dec 14 09:32:28 ndhcps
Info: sending ACK of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 09:32:28 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.142 from 7c:f6:66:84:cc:8d.
Dec 14 09:32:28 ndhcps
Info: making OFFER of 192.168.0.142 to 7c:f6:66:84:cc:8d.
Dec 14 09:32:28 ndhcps
Info: DHCPDISCOVER received from 7c:f6:66:84:cc:8d.
Dec 14 09:32:28 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) set key done in WPA2/WPA2PSK.
Dec 14 09:32:28 ndm
Info: Network::Interface::Mtk::WifiMonitor: “WifiMaster0/AccessPoint0”: STA(7c:f6:66:84:cc:8d) had associated.
Dec 14 09:27:57 ndhcps
Info: sending ACK of 192.168.0.135 to 50:ff:20:5c:83:16.
Dec 14 09:27:57 ndhcps
Info: sending ACK of 10.1.30.142 to 52:ff:20:5c:83:15.
Dec 14 09:27:57 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 192.168.0.135 from 50:ff:20:5c:83:16.
Dec 14 09:27:57 ndhcps
Info: making OFFER of 192.168.0.135 to 50:ff:20:5c:83:16.
Dec 14 09:27:57 ndhcps
Info: DHCPDISCOVER received from 50:ff:20:5c:83:16.
Dec 14 09:27:57 ndhcps
Info: DHCPREQUEST received (STATE_SELECTING) for 10.1.3