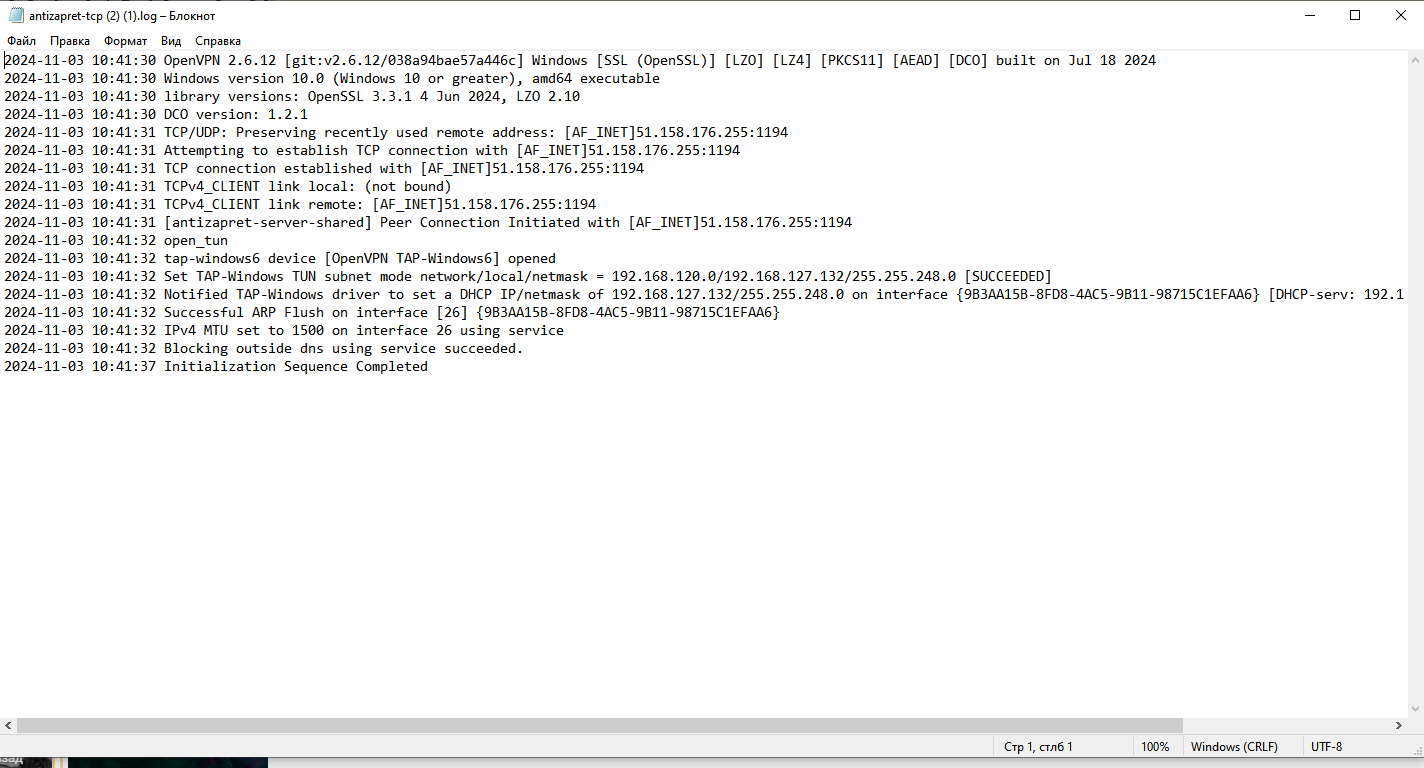
функция выключена
вот логи журнала после того как добавил
Sat Nov 2 12:38:47 2024 daemon.warn openvpn(OVPN)[5372]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1559', remote='link-mtu 1543'
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: Control Channel: TLSv1.2, cipher TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384, 2048 bit key
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: [antizapret-server-shared] Peer Connection Initiated with [AF_INET]141.95.17.71:1194
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: PUSH: Received control message: 'PUSH_REPLY,route 10.224.0.0 255.254.0.0,dhcp-option DNS 192.168.104.1,block-outside-dns,route-gateway 192.168.104.1,topology subnet,ping 110,ping-restart 360,socket-flags TCP_NODELAY,route 103.246.200.0 255.255.252.0,route 178.239.88.0 255.255.248.0,route 185.104.45.0 255.255.255.0,route 193.105.213.36 255.255.255.252,route 203.104.128.0 255.255.240.0,route 203.104.144.0 255.255.248.0,route 203.104.152.0 255.255.252.0,route 68.171.224.0 255.255.224.0,route 74.82.64.0 255.255.224.0,ifconfig 192.168.106.13 255.255.248.0,peer-id 0,cipher AES-128-GCM'
Sat Nov 2 12:38:47 2024 daemon.err openvpn(OVPN)[5372]: Options error: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:3: block-outside-dns (2.5.3)
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: timers and/or timeouts modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: --socket-flags option modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: --ifconfig/up options modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: route options modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: route-related options modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: peer-id set
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: adjusting link_mtu to 1626
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: data channel crypto options modified
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: Data Channel: using negotiated cipher 'AES-128-GCM'
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: Data Channel MTU parms [ L:1554 D:1450 EF:54 EB:406 ET:0 EL:3 ]
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_best_gw result: via 10.128.0.137 dev pptp-vpn
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: TUN/TAP device ovpn_OVPN opened
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: do_ifconfig, ipv4=1, ipv6=0
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_iface_mtu_set: mtu 1500 for ovpn_OVPN
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_iface_up: set ovpn_OVPN up
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_addr_v4_add: 192.168.106.13/21 dev ovpn_OVPN
Sat Nov 2 12:38:47 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is enabled
Sat Nov 2 12:38:47 2024 daemon.notice netifd: Network device 'ovpn_OVPN' link is up
Sat Nov 2 12:38:47 2024 daemon.notice netifd: Interface 'ovpn_OVPN' has link connectivity
Sat Nov 2 12:38:47 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is setting up now
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: /usr/libexec/openvpn-hotplug up OVPN ovpn_OVPN 1500 1554 192.168.106.13 255.255.248.0 init
Sat Nov 2 12:38:47 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is now up
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 8.8.8.8/32 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 77.88.8.8/32 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 10.224.0.0/15 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 103.246.200.0/22 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 178.239.88.0/21 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 185.104.45.0/24 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 193.105.213.36/30 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 203.104.128.0/20 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 203.104.144.0/21 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 203.104.152.0/22 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 68.171.224.0/19 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 74.82.64.0/19 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:38:47 2024 daemon.warn openvpn(OVPN)[5372]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sat Nov 2 12:38:47 2024 daemon.notice openvpn(OVPN)[5372]: Initialization Sequence Completed
Sat Nov 2 12:38:47 2024 daemon.notice procd: /etc/init.d/network: kill fwdd daemon and remove mtfwd module
Sat Nov 2 12:38:47 2024 user.notice firewall: Reloading firewall due to ifup of ovpn_OVPN (ovpn_OVPN)
Sat Nov 2 12:38:50 2024 daemon.notice procd: /etc/init.d/network: Non MAP mode
Sat Nov 2 12:38:53 2024 daemon.notice procd: /etc/init.d/network: net link socket didn't created.
Sat Nov 2 12:39:23 2024 daemon.info dnsmasq-dhcp[4292]: DHCPREQUEST(br-lan) 192.168.1.181 36:ac:71:3b:e2:d5
Sat Nov 2 12:39:23 2024 daemon.info dnsmasq-dhcp[4292]: DHCPACK(br-lan) 192.168.1.181 36:ac:71:3b:e2:d5
Sat Nov 2 12:47:09 2024 daemon.info pppd[3538]: System time change detected.
Sat Nov 2 12:47:10 2024 daemon.notice openvpn(OVPN)[5372]: [antizapret-server-shared] Inactivity timeout (--ping-restart), restarting
Sat Nov 2 12:47:10 2024 daemon.notice openvpn(OVPN)[5372]: TCP/UDP: Closing socket
Sat Nov 2 12:47:10 2024 daemon.notice openvpn(OVPN)[5372]: SIGUSR1[soft,ping-restart] received, process restarting
Sat Nov 2 12:47:10 2024 daemon.notice openvpn(OVPN)[5372]: Restart pause, 5 second(s)
Sat Nov 2 12:47:15 2024 daemon.warn openvpn(OVPN)[5372]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Re-using SSL/TLS context
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Control Channel MTU parms [ L:1623 D:1210 EF:40 EB:0 ET:0 EL:3 ]
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Data Channel MTU parms [ L:1623 D:1450 EF:123 EB:406 ET:0 EL:3 ]
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_CLIENT,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_SERVER,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: TCP/UDP: Preserving recently used remote address: [AF_INET]141.95.17.71:1194
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Socket Buffers: R=[87380->87380] S=[16384->16384]
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Attempting to establish TCP connection with [AF_INET]141.95.17.71:1194 [nonblock]
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: TCP connection established with [AF_INET]141.95.17.71:1194
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: TCP_CLIENT link local: (not bound)
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: TCP_CLIENT link remote: [AF_INET]141.95.17.71:1194
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: TLS: Initial packet from [AF_INET]141.95.17.71:1194, sid=0ff94e79 0326db55
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: VERIFY OK: depth=1, CN=AntiZapret CA2
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Validating certificate key usage
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: VERIFY KU OK
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: Validating certificate extended key usage
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: VERIFY EKU OK
Sat Nov 2 12:47:15 2024 daemon.notice openvpn(OVPN)[5372]: VERIFY OK: depth=0, CN=antizapret-server-shared
Sat Nov 2 12:47:16 2024 daemon.warn openvpn(OVPN)[5372]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1559', remote='link-mtu 1543'
Sat Nov 2 12:47:16 2024 daemon.notice openvpn(OVPN)[5372]: Control Channel: TLSv1.2, cipher TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384, 2048 bit key
Sat Nov 2 12:47:16 2024 daemon.notice openvpn(OVPN)[5372]: [antizapret-server-shared] Peer Connection Initiated with [AF_INET]141.95.17.71:1194
Sat Nov 2 12:47:17 2024 daemon.notice openvpn(OVPN)[5372]: SENT CONTROL [antizapret-server-shared]: 'PUSH_REQUEST' (status=1)
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: PUSH: Received control message: 'PUSH_REPLY,route 10.224.0.0 255.254.0.0,dhcp-option DNS 192.168.104.1,block-outside-dns,route-gateway 192.168.104.1,topology subnet,ping 110,ping-restart 360,socket-flags TCP_NODELAY,route 103.246.200.0 255.255.252.0,route 178.239.88.0 255.255.248.0,route 185.104.45.0 255.255.255.0,route 193.105.213.36 255.255.255.252,route 203.104.128.0 255.255.240.0,route 203.104.144.0 255.255.248.0,route 203.104.152.0 255.255.252.0,route 68.171.224.0 255.255.224.0,route 74.82.64.0 255.255.224.0,ifconfig 192.168.110.33 255.255.248.0,peer-id 0,cipher AES-128-GCM'
Sat Nov 2 12:47:18 2024 daemon.err openvpn(OVPN)[5372]: Options error: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:3: block-outside-dns (2.5.3)
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: timers and/or timeouts modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: --socket-flags option modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: --ifconfig/up options modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: route options modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: route-related options modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: peer-id set
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: adjusting link_mtu to 1626
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: OPTIONS IMPORT: data channel crypto options modified
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: Data Channel: using negotiated cipher 'AES-128-GCM'
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: Data Channel MTU parms [ L:1554 D:1450 EF:54 EB:406 ET:0 EL:3 ]
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: Preserving previous TUN/TAP instance: ovpn_OVPN
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: NOTE: Pulled options changed on restart, will need to close and reopen TUN/TAP device.
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 8.8.8.8/32 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 77.88.8.8/32 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 10.224.0.0/15 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 103.246.200.0/22 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 178.239.88.0/21 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 185.104.45.0/24 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 193.105.213.36/30 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 203.104.128.0/20 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 203.104.144.0/21 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 203.104.152.0/22 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 68.171.224.0/19 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_del: 74.82.64.0/19 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: Closing TUN/TAP interface
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: net_addr_v4_del: 192.168.106.13 dev ovpn_OVPN
Sat Nov 2 12:47:18 2024 daemon.notice netifd: Network device 'ovpn_OVPN' link is down
Sat Nov 2 12:47:18 2024 daemon.notice netifd: Interface 'ovpn_OVPN' has link connectivity loss
Sat Nov 2 12:47:18 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is now down
Sat Nov 2 12:47:18 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is disabled
Sat Nov 2 12:47:18 2024 daemon.notice openvpn(OVPN)[5372]: /usr/libexec/openvpn-hotplug down OVPN ovpn_OVPN 1500 1554 192.168.106.13 255.255.248.0 init
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_best_gw result: via 10.128.0.137 dev pptp-vpn
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: TUN/TAP device ovpn_OVPN opened
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: do_ifconfig, ipv4=1, ipv6=0
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_iface_mtu_set: mtu 1500 for ovpn_OVPN
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_iface_up: set ovpn_OVPN up
Sat Nov 2 12:47:19 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is enabled
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_addr_v4_add: 192.168.110.33/21 dev ovpn_OVPN
Sat Nov 2 12:47:19 2024 daemon.notice netifd: Network device 'ovpn_OVPN' link is up
Sat Nov 2 12:47:19 2024 daemon.notice netifd: Interface 'ovpn_OVPN' has link connectivity
Sat Nov 2 12:47:19 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is setting up now
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: /usr/libexec/openvpn-hotplug up OVPN ovpn_OVPN 1500 1554 192.168.110.33 255.255.248.0 init
Sat Nov 2 12:47:19 2024 daemon.notice netifd: Interface 'ovpn_OVPN' is now up
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 8.8.8.8/32 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 77.88.8.8/32 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 10.224.0.0/15 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 103.246.200.0/22 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 178.239.88.0/21 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 185.104.45.0/24 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 193.105.213.36/30 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 203.104.128.0/20 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 203.104.144.0/21 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 203.104.152.0/22 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 68.171.224.0/19 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: net_route_v4_add: 74.82.64.0/19 via 192.168.104.1 dev [NULL] table 0 metric -1
Sat Nov 2 12:47:19 2024 daemon.notice openvpn(OVPN)[5372]: Initialization Sequence Completed
Sat Nov 2 12:47:19 2024 user.notice firewall: Reloading firewall due to ifup of ovpn_OVPN (ovpn_OVPN)
Sat Nov 2 12:50:50 2024 daemon.warn dnsmasq[4292]: Ignoring query from non-local network